- Usage
- Self-Hosted Setup
Prerequisites:
- Set up and add envars to Infisical Cloud.
- Set up Azure and have an existing App Configuration instance.
- User setting up the integration on Infisical must have the
App Configuration Data Ownerrole for the intended Azure App Configuration instance. - Azure App Configuration instance must be reachable by Infisical.
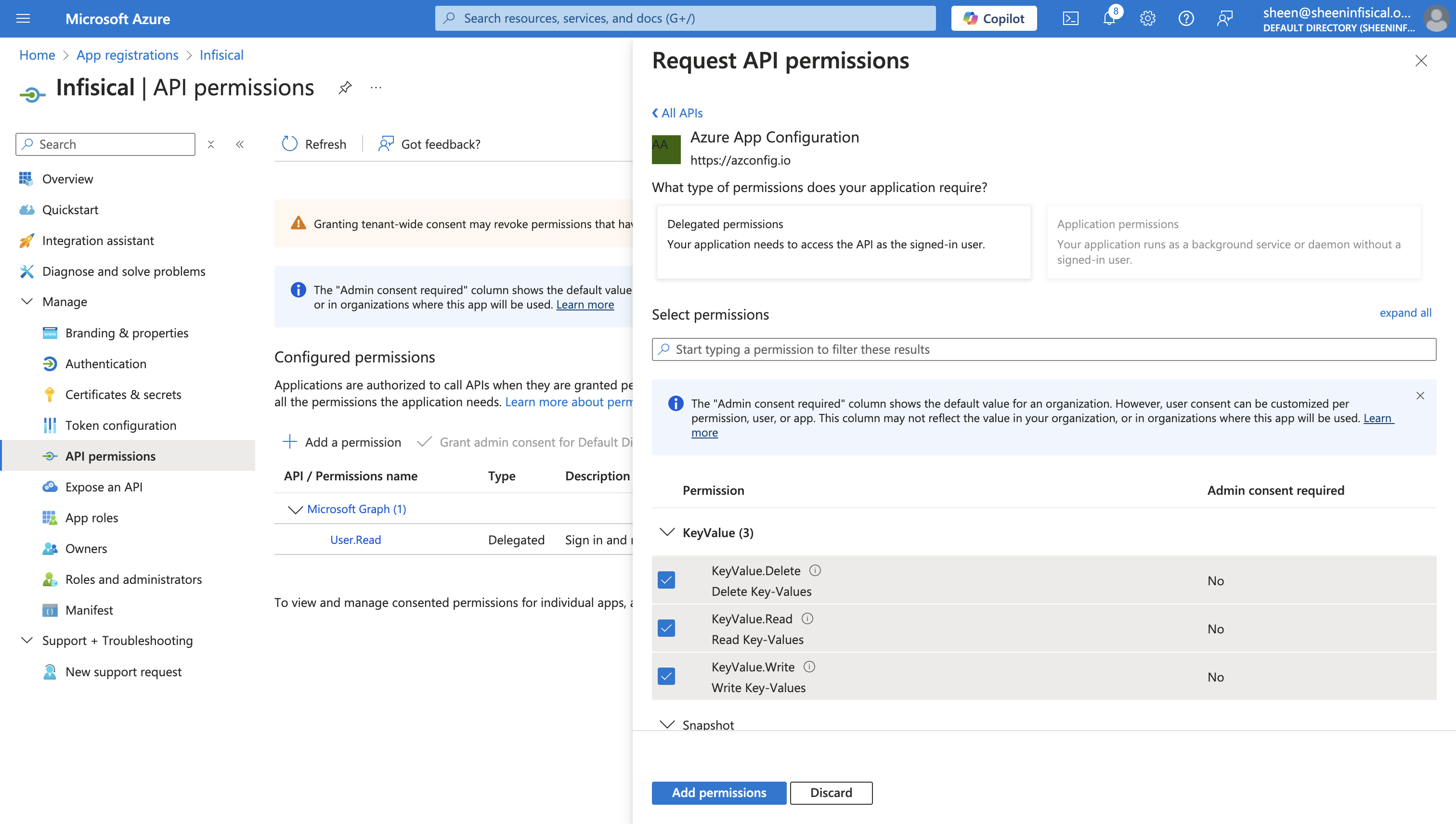
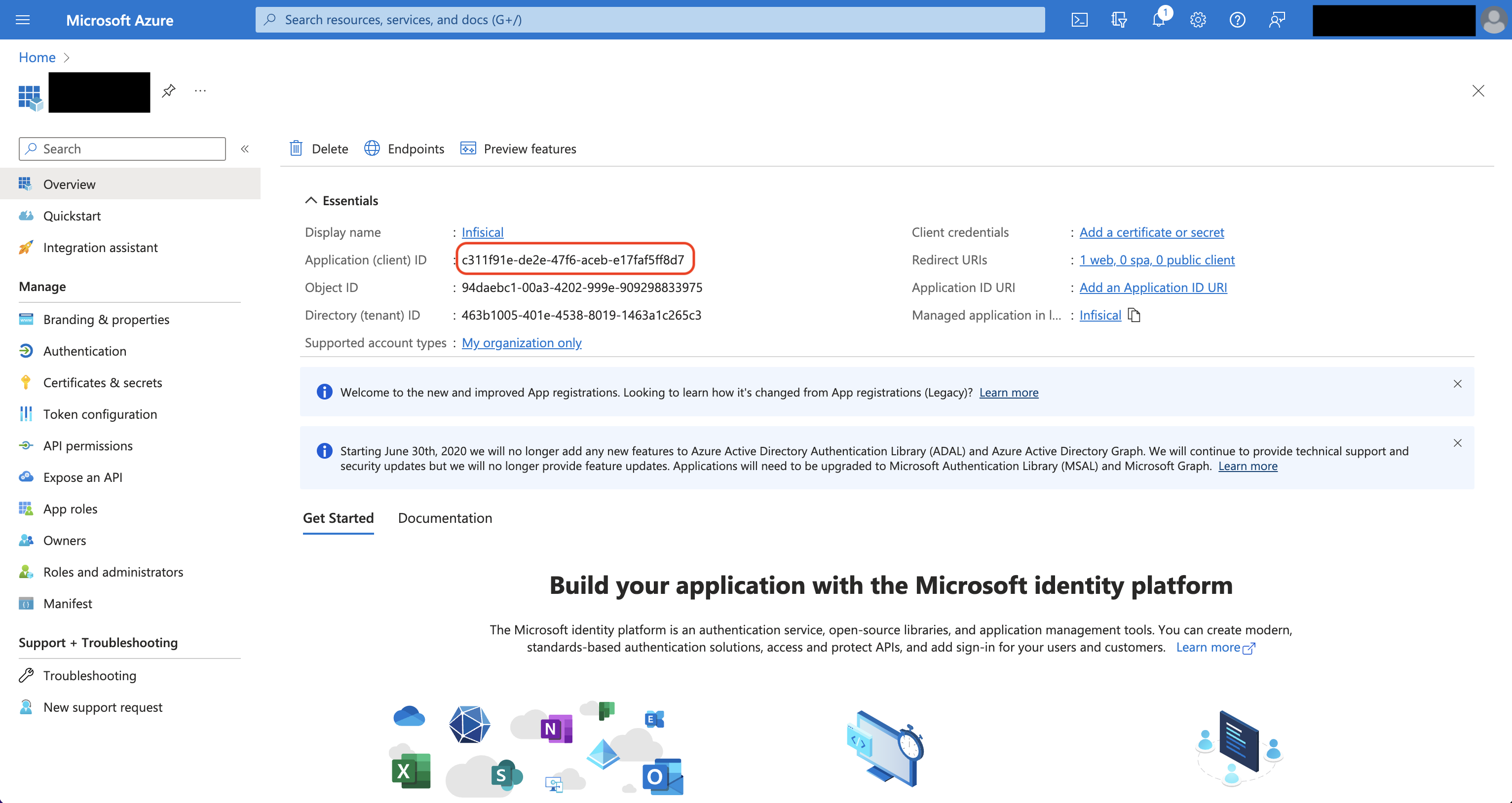
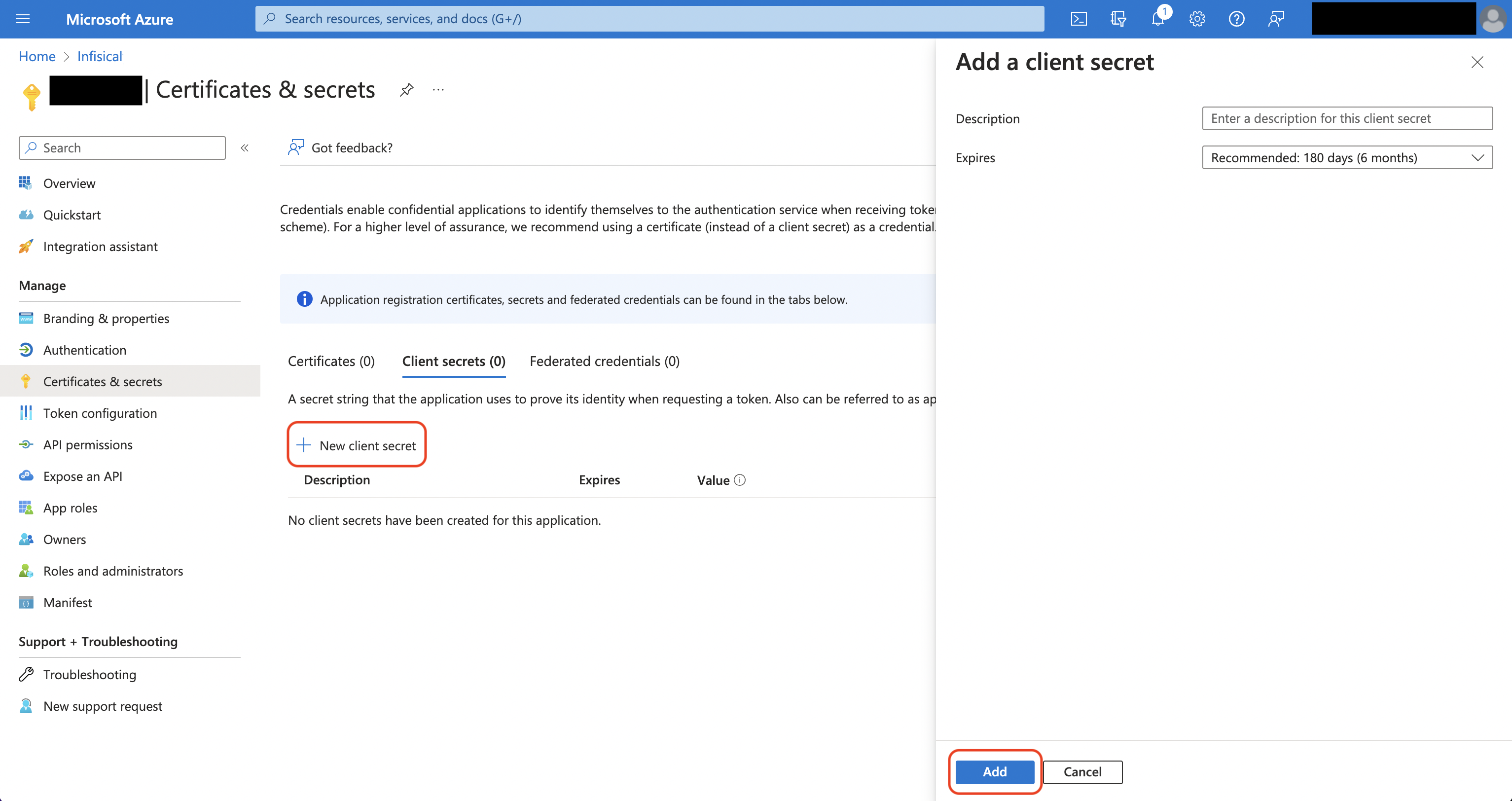
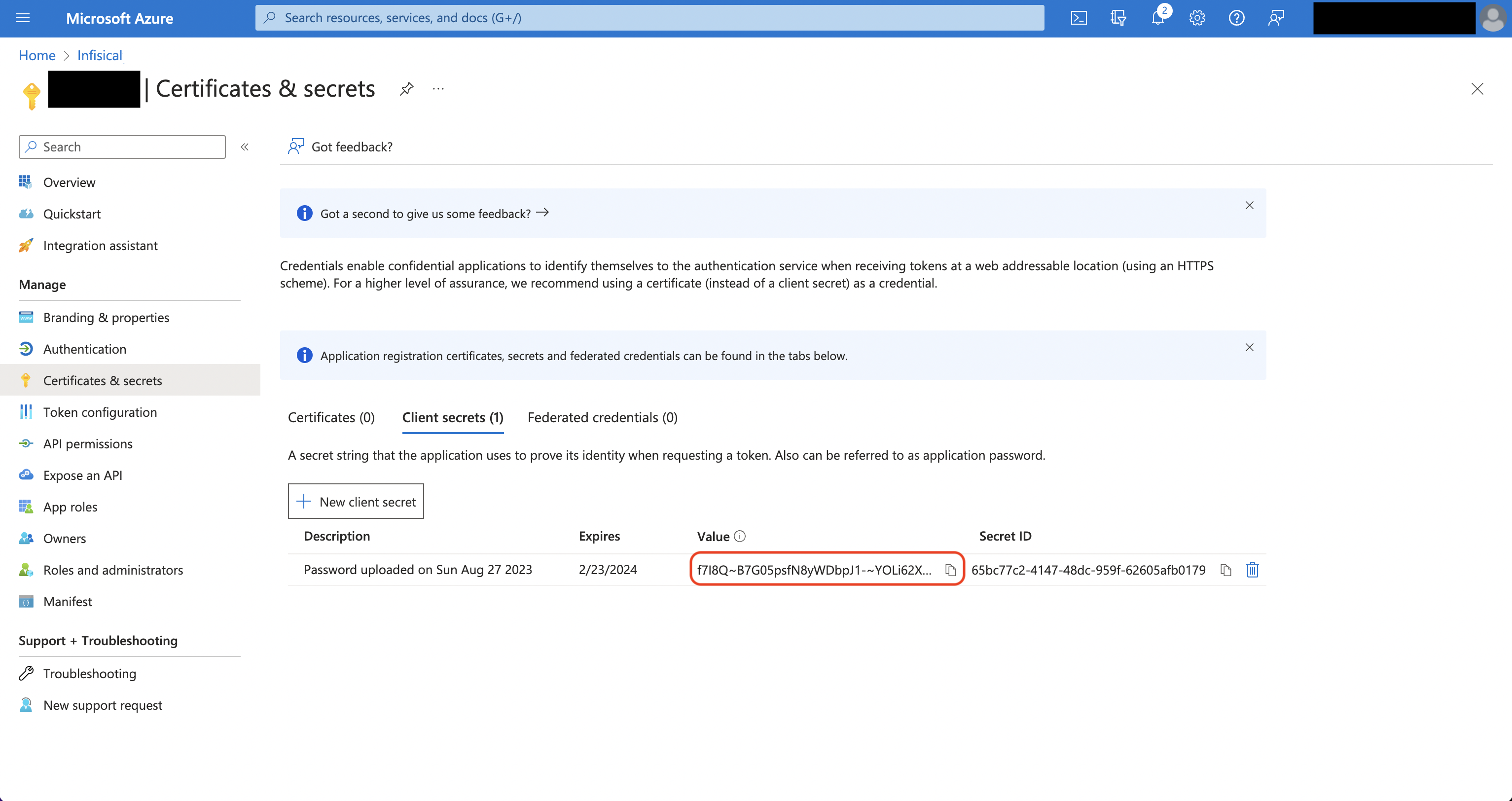
Authorize Infisical for Azure App Configuration
Navigate to your project’s integrations tab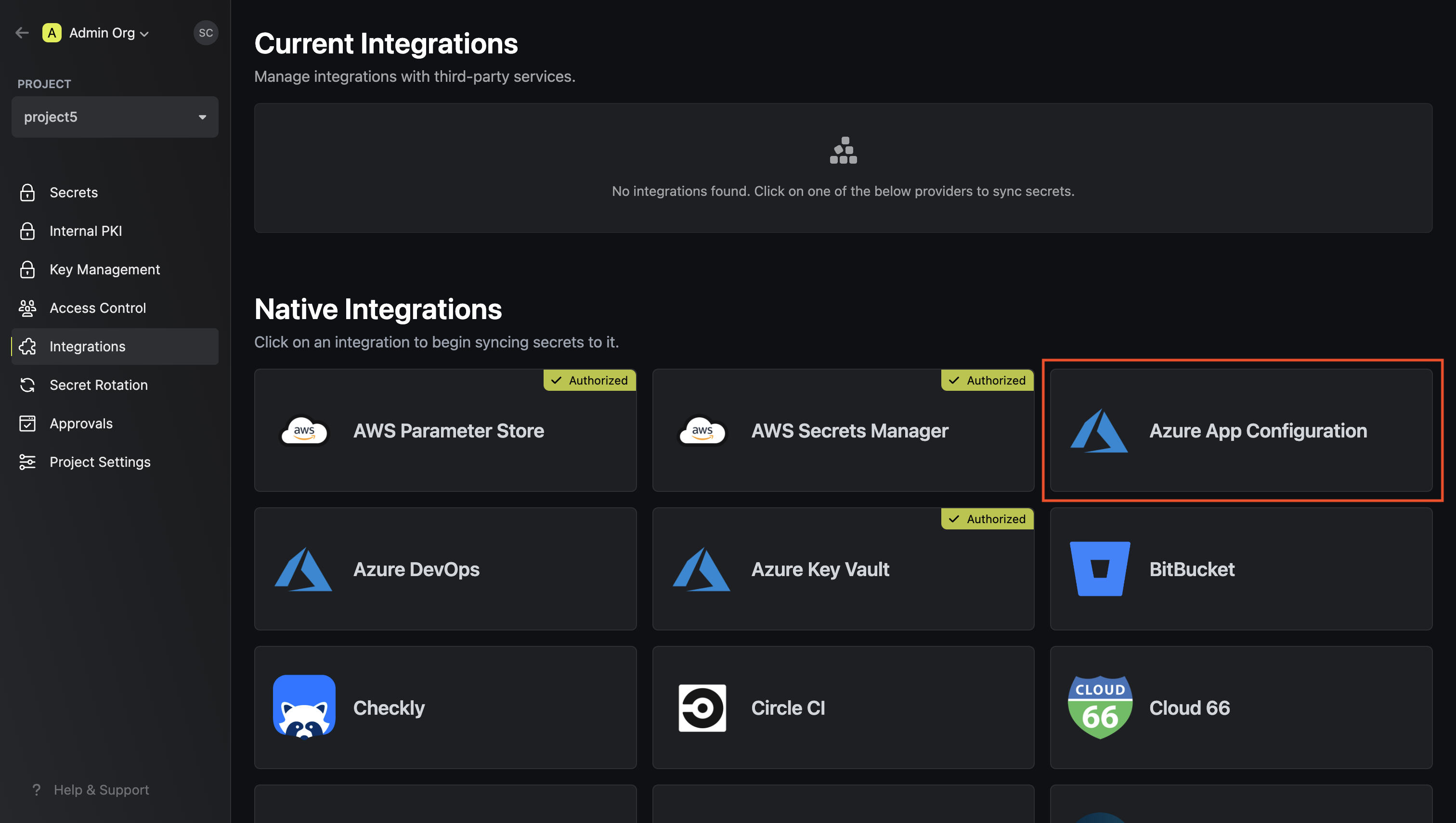 Press on the Azure App Configuration tile and grant Infisical access to App Configuration.
Press on the Azure App Configuration tile and grant Infisical access to App Configuration.
 Press on the Azure App Configuration tile and grant Infisical access to App Configuration.
Press on the Azure App Configuration tile and grant Infisical access to App Configuration.Start integration
Obtain the Azure App Configuration endpoint from the overview tab.
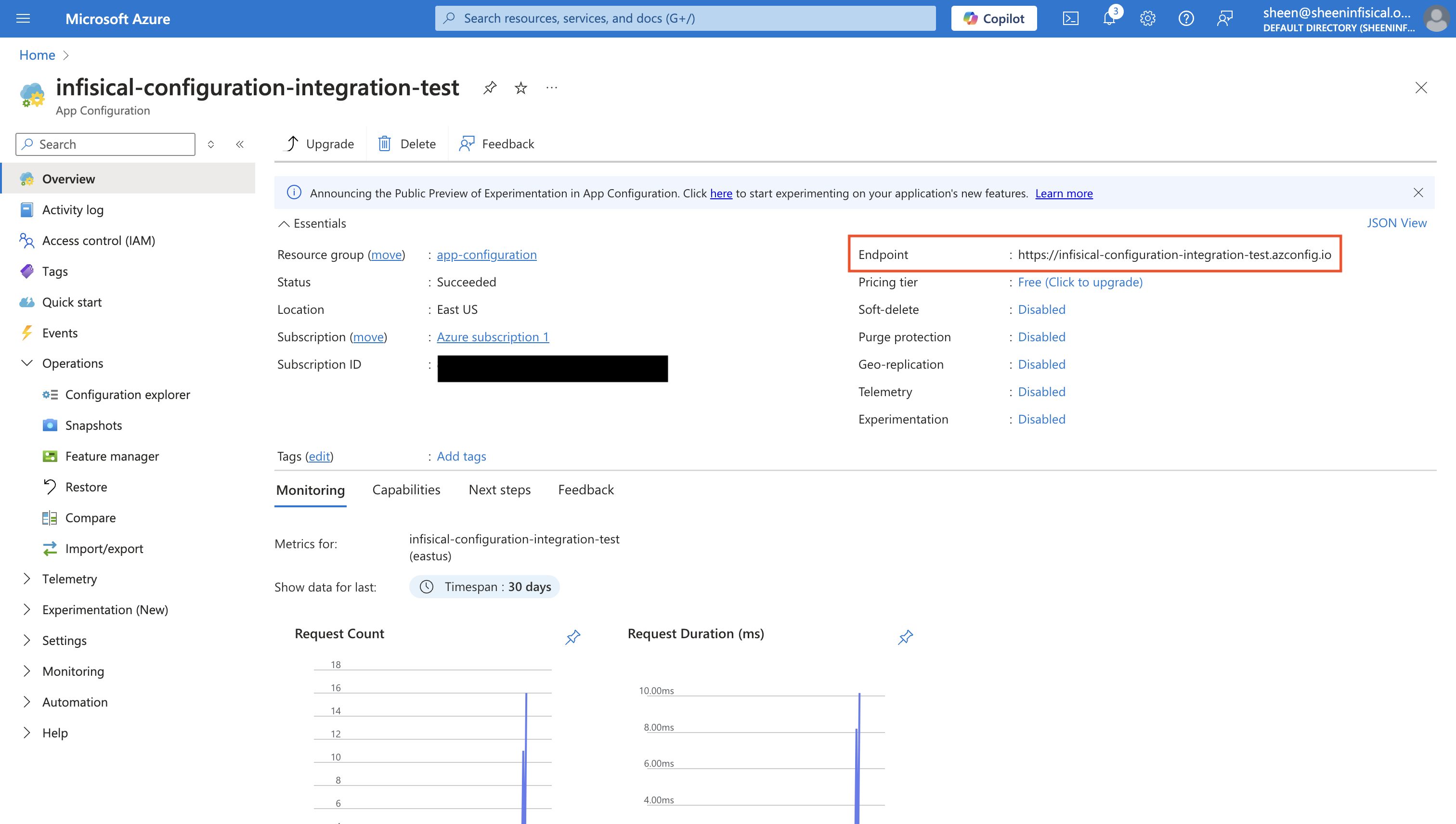 Select which Infisical environment secrets you want to sync to your Azure App Configuration. Then, input your App Configuration instance endpoint. Optionally, you can define a prefix for your secrets which will be appended to the keys upon syncing.
Select which Infisical environment secrets you want to sync to your Azure App Configuration. Then, input your App Configuration instance endpoint. Optionally, you can define a prefix for your secrets which will be appended to the keys upon syncing.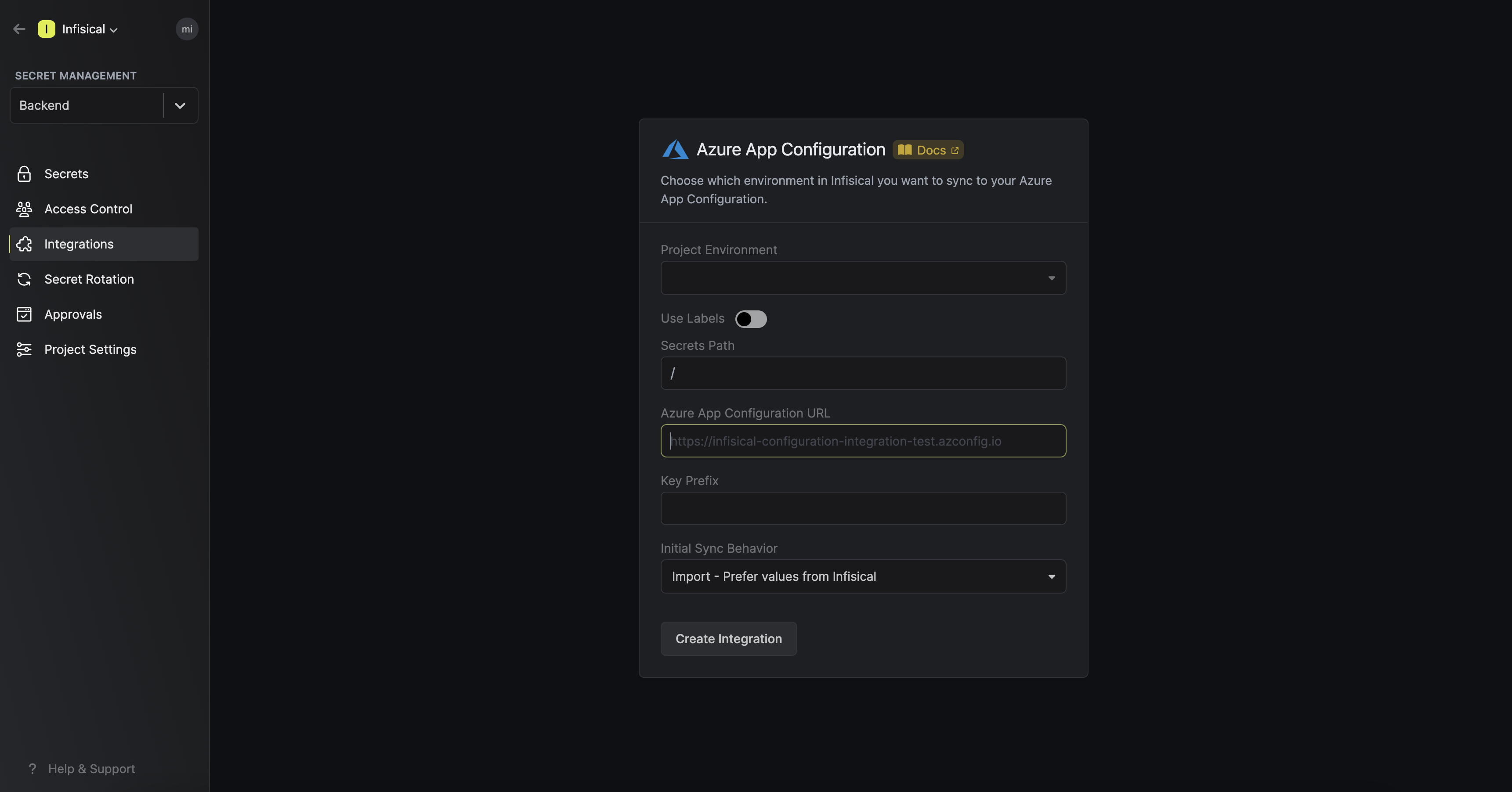 Press create integration to start syncing secrets to Azure App Configuration.
Press create integration to start syncing secrets to Azure App Configuration.
 Select which Infisical environment secrets you want to sync to your Azure App Configuration. Then, input your App Configuration instance endpoint. Optionally, you can define a prefix for your secrets which will be appended to the keys upon syncing.
Select which Infisical environment secrets you want to sync to your Azure App Configuration. Then, input your App Configuration instance endpoint. Optionally, you can define a prefix for your secrets which will be appended to the keys upon syncing. Press create integration to start syncing secrets to Azure App Configuration.
Press create integration to start syncing secrets to Azure App Configuration.Additional Configuration
Azure references
When adding secrets in Infisical that reference Azure Key Vault secrets, Infisical will automatically sets the content type toapplication/vnd.microsoft.appconfig.keyvaultref+json;charset=utf-8 in Azure App Configuration.
The following reference formats are automatically detected when added on Infisical’s side:{ "uri": "https://my-key-vault.vault.azure.net/secrets/my-secret" }https://my-key-vault.vault.azure.net/secrets/my-secret
Azure Labels
You can sync secrets from Infisical to Azure with custom labels by enabling theUse Labels option during setup:When enabled: Secrets will be pushed to Azure with your specified labelWhen disabled: Secrets will be pushed with an empty (null) labelIf you have set the initial sync to
import have behavior, the label selection affects which secrets are imported from Azure:- With
Use Labelsdisabled: Only secrets with empty labels are imported on initial sync - With
Use Labelsenabled: Only secrets matching your specified label are imported on initial sync