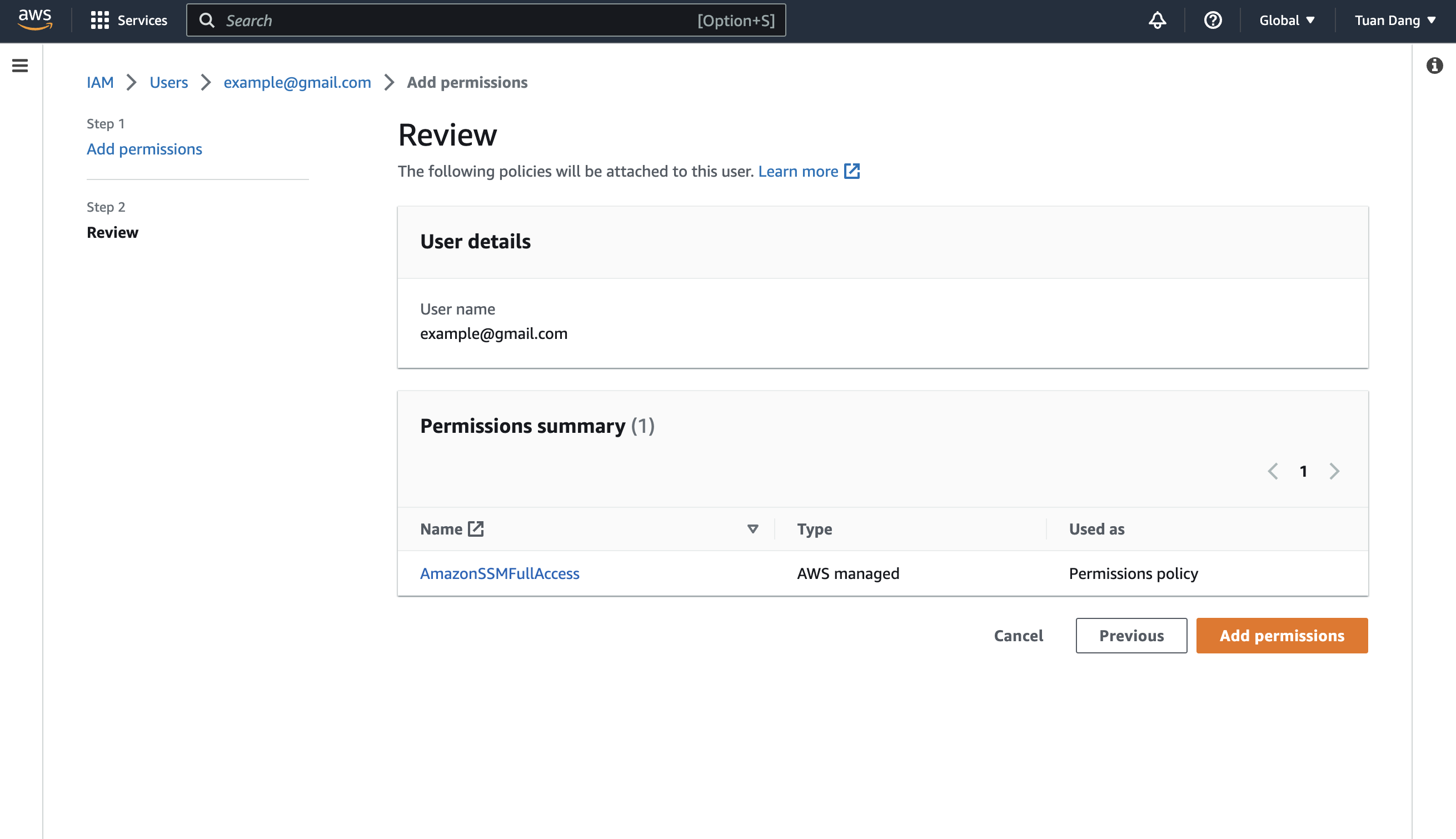
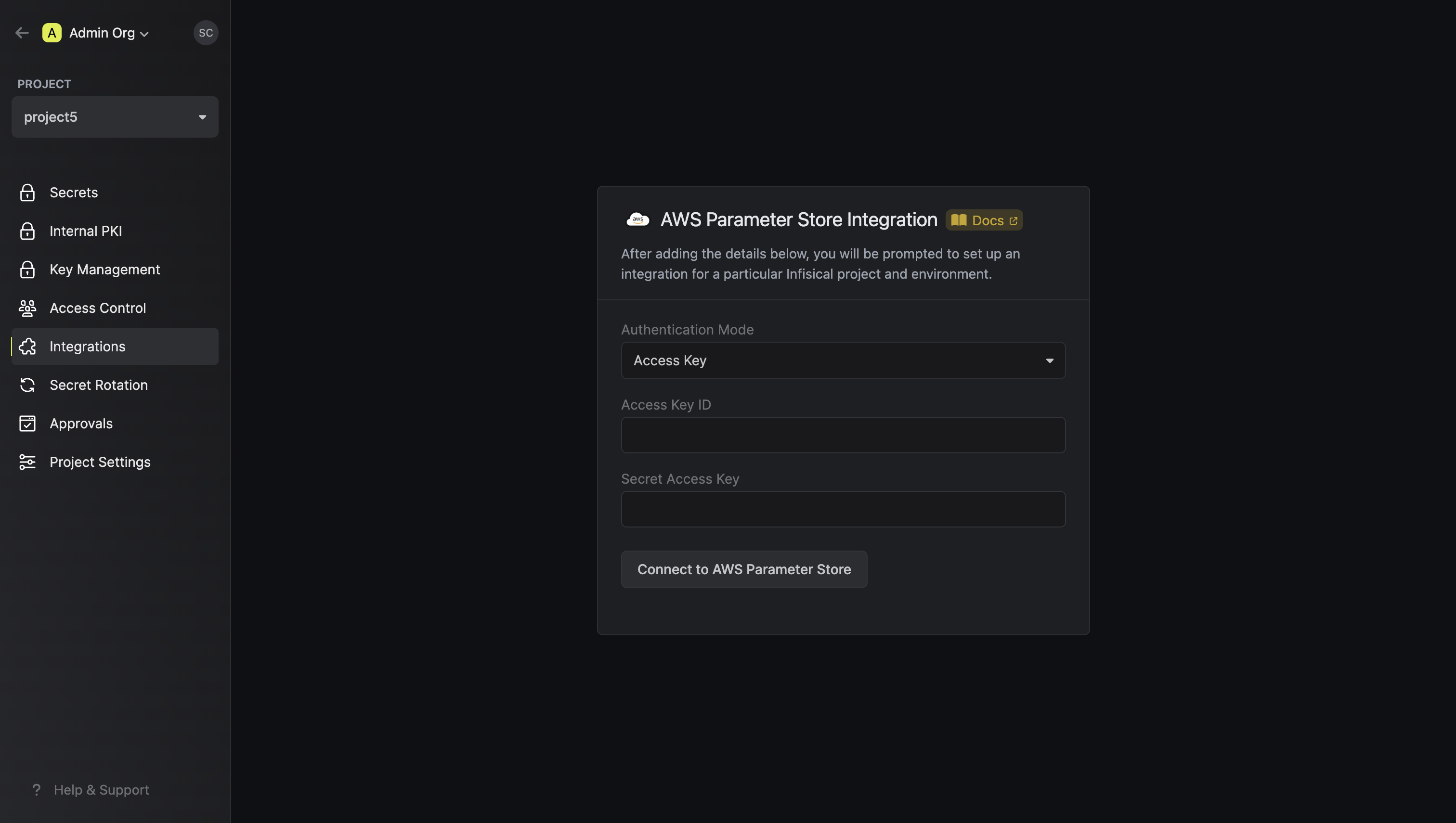
- Assume Role (Recommended)
- Access Key
Infisical will assume the provided role in your AWS account securely, without the need to share any credentials.Prerequisites:
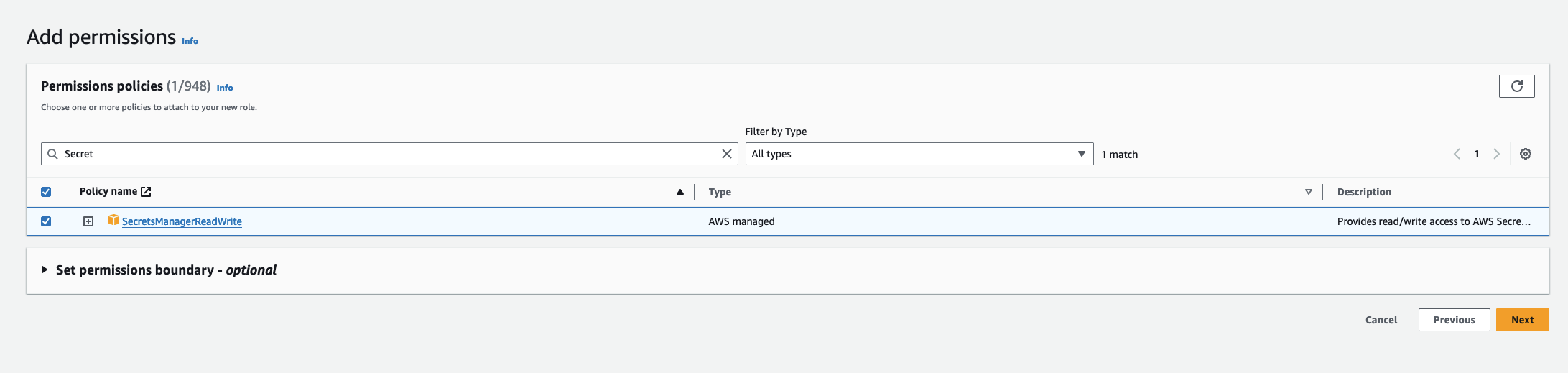 Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Parameter Store:
Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Parameter Store:
- Set up and add envars to Infisical Cloud
Self-Hosted Users
Self-Hosted Users
To connect your Infisical instance with AWS, you need to set up an AWS IAM User account that can assume the AWS IAM Role for the integration.If your instance is deployed on AWS, the aws-sdk will automatically retrieve the credentials. Ensure that you assign the provided permission policy to your deployed instance, such as ECS or EC2.The following steps are for instances not deployed on AWS
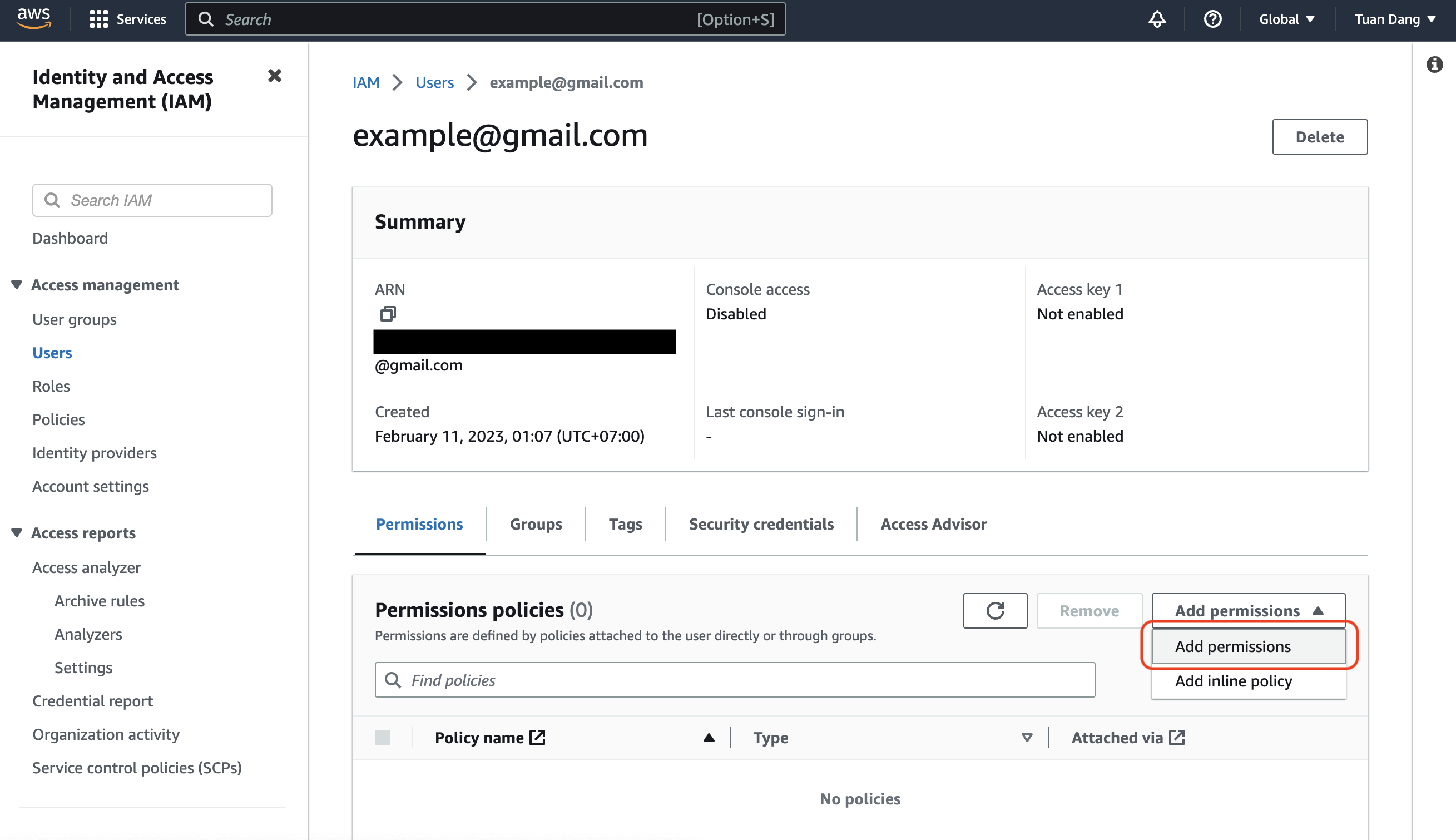
Create an IAM User
Navigate to Create IAM User in your AWS Console.
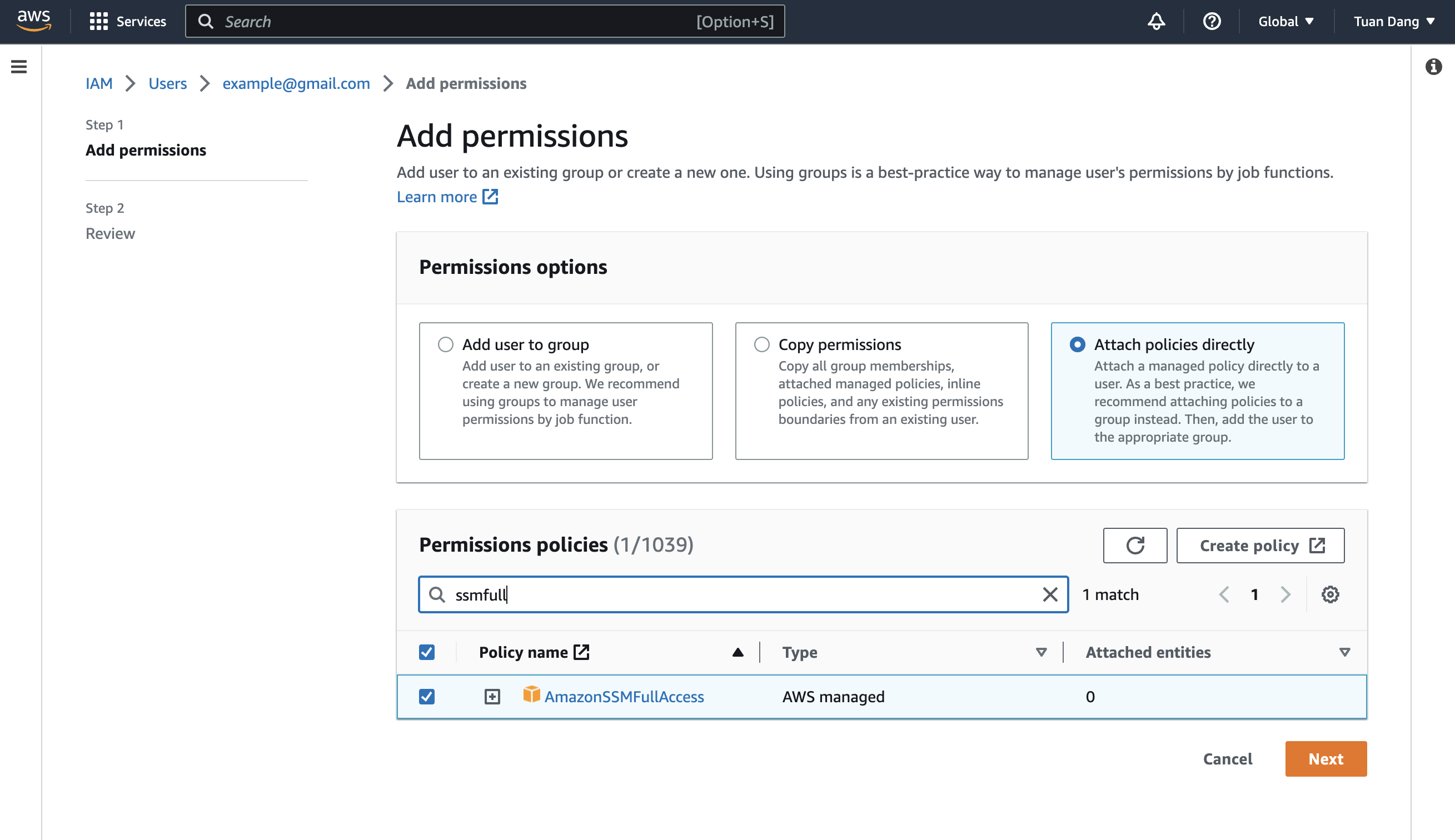
Create an Inline Policy
Attach the following inline permission policy to the IAM User to allow it to assume any IAM Roles:
Obtain the IAM User Credentials
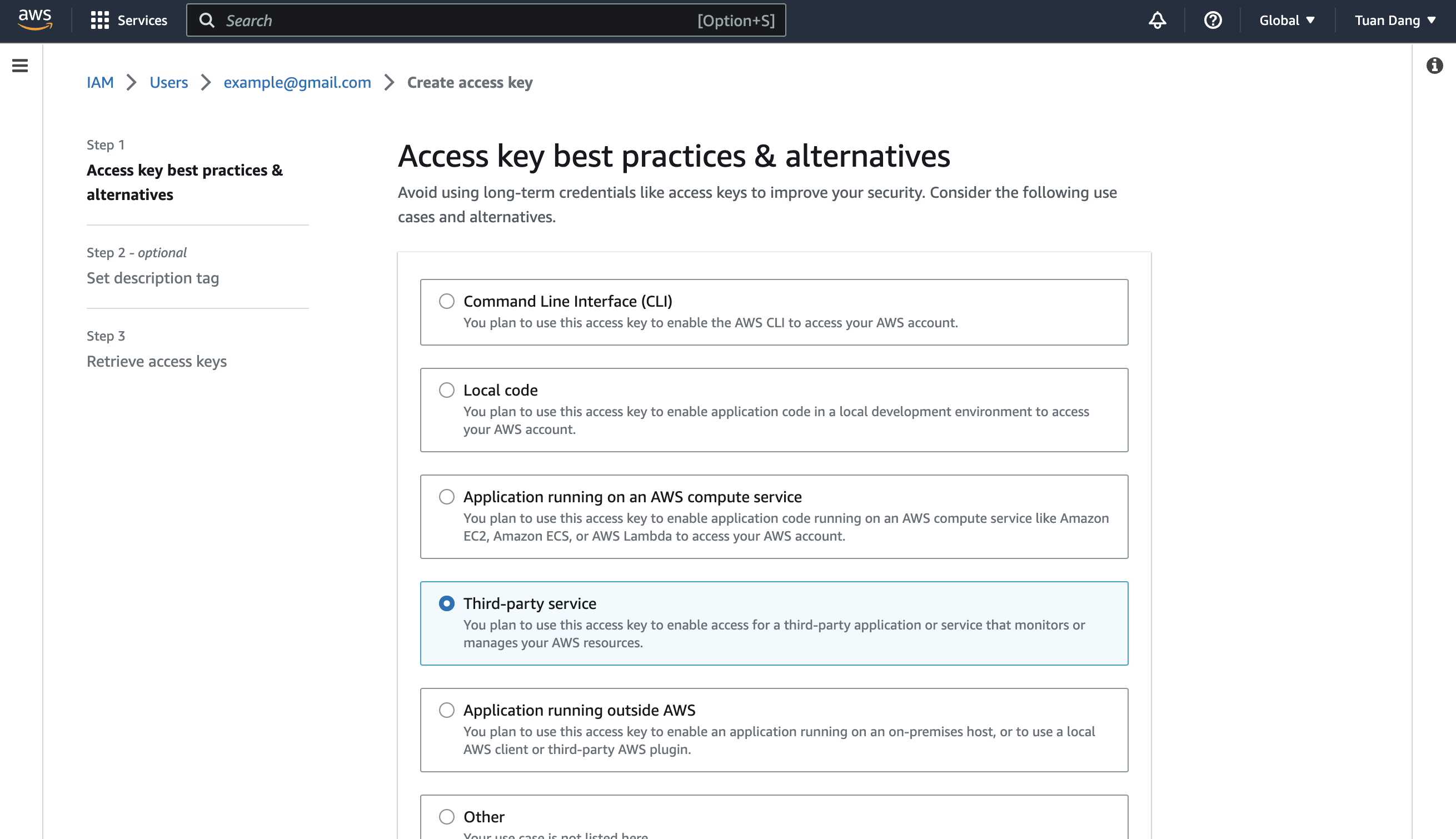
Obtain the AWS access key ID and secret access key for your IAM User by navigating to IAM > Users > [Your User] > Security credentials > Access keys.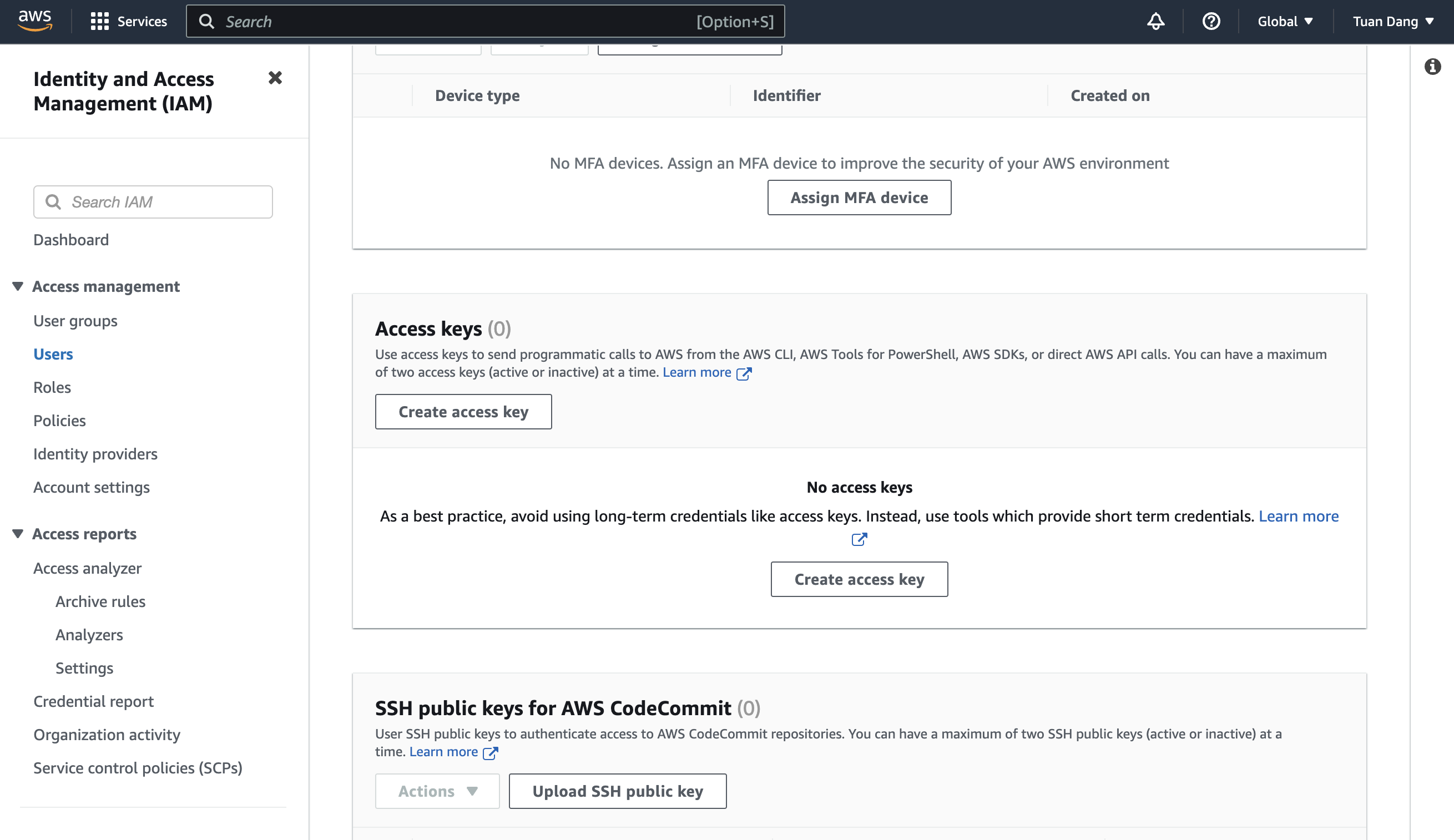



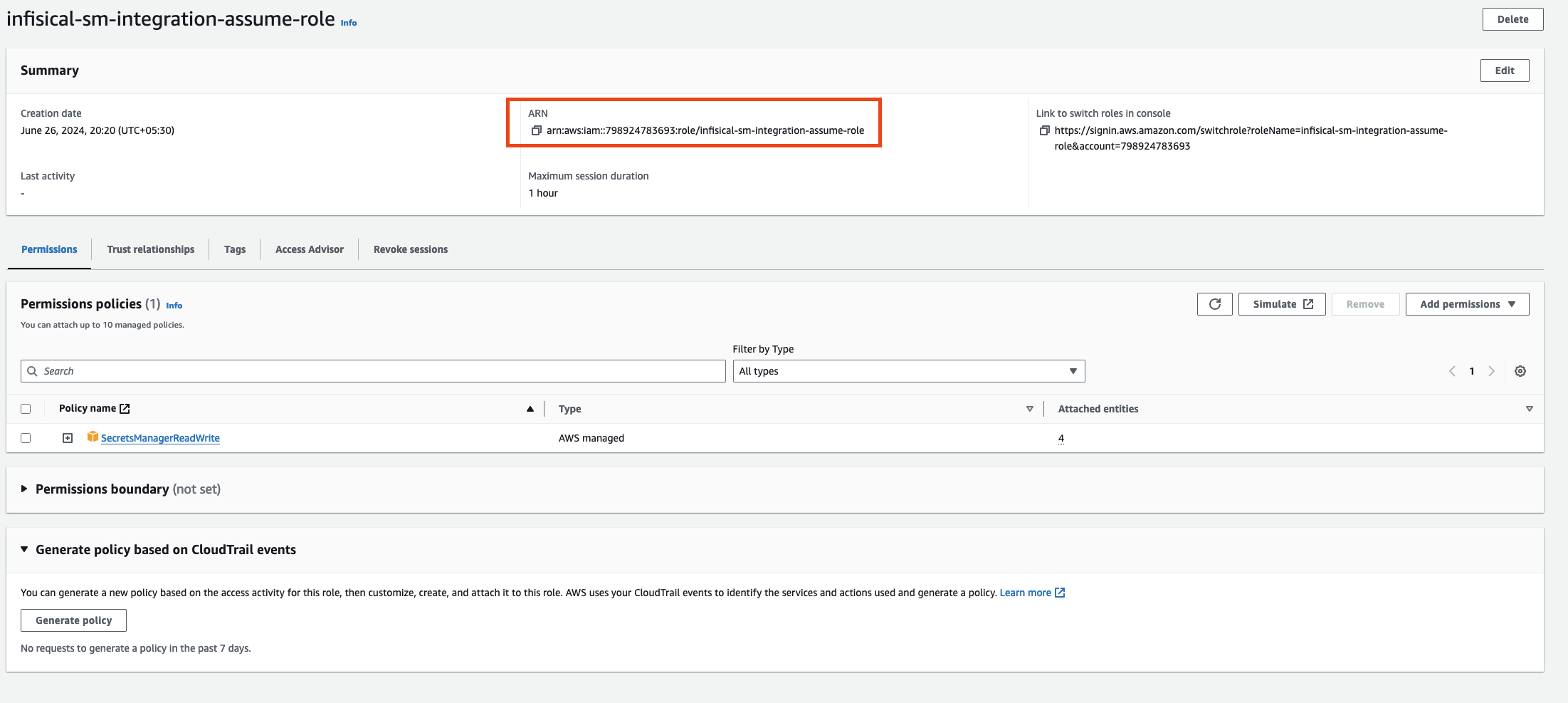
Create the Managing User IAM Role for AWS Parameter Store
-
Navigate to the Create IAM Role page in your AWS Console.
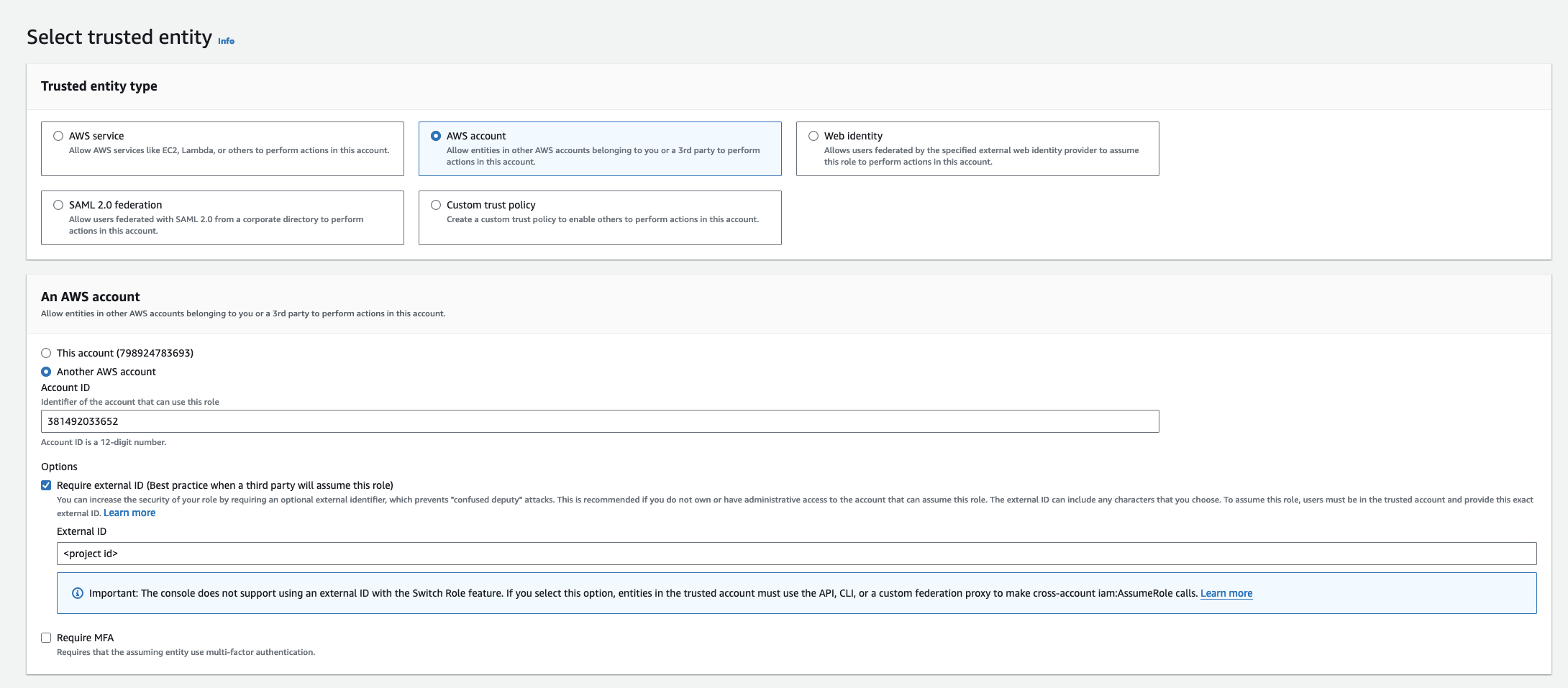
- Select AWS Account as the Trusted Entity Type.
- Choose Another AWS Account and enter 381492033652 (Infisical AWS Account ID). This restricts the role to be assumed only by Infisical. If self-hosting, provide your AWS account number instead.
- Optionally, enable Require external ID and enter your project ID to further enhance security.
Add Required Permissions for the IAM Role
 Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Parameter Store:
Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Parameter Store:Authorize Infisical for AWS Parameter Store
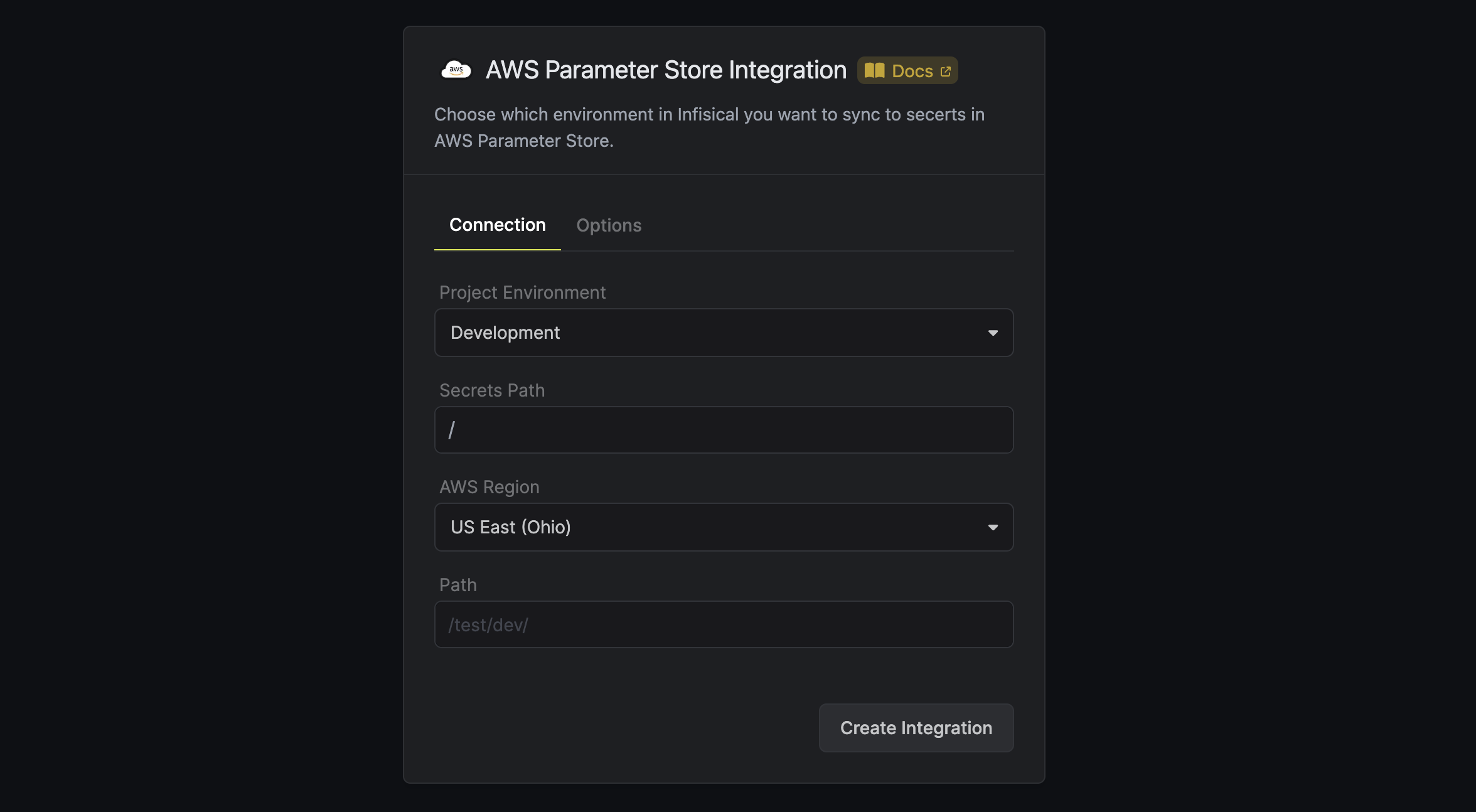
- Navigate to your project’s integrations tab in Infisical.
-
Click on the AWS Parameter Store tile.

-
Select the AWS Assume Role option.
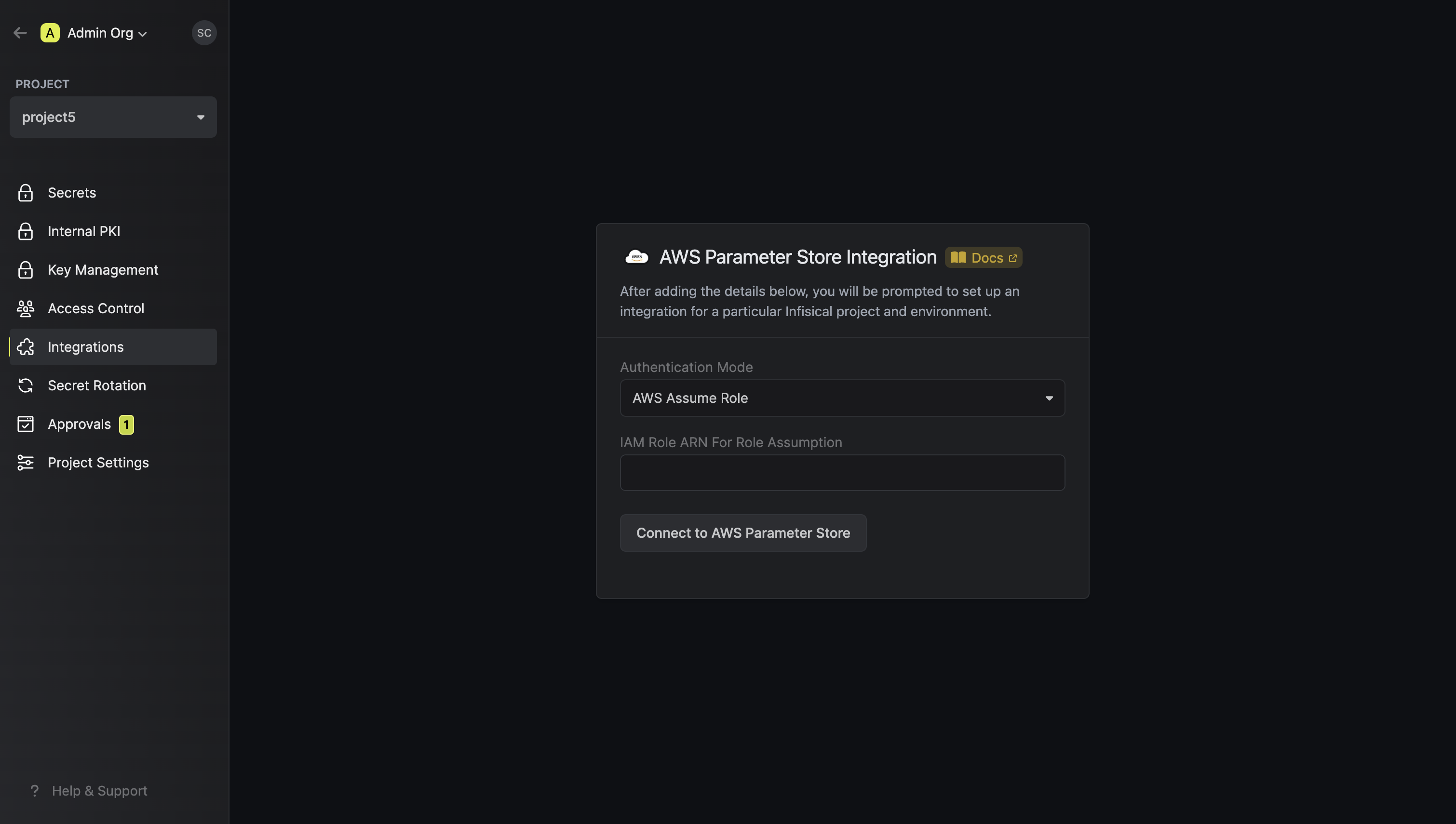
- Provide the AWS IAM Role ARN obtained from the previous step and press connect.