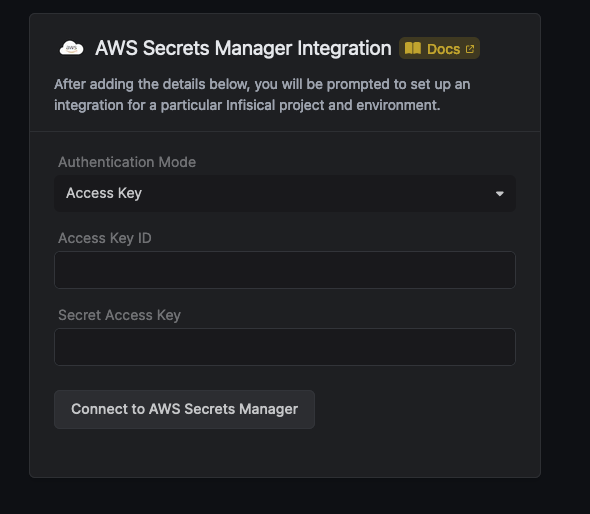
- Assume Role (Recommended)
- Access Key
Infisical will assume the provided role in your AWS account securely, without the need to share any credentials.Prerequisites:
 Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Secrets Manager:
Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Secrets Manager:
- Set up and add envars to Infisical Cloud
Self-Hosted Users
Self-Hosted Users
To connect your Infisical instance with AWS, you need to set up an AWS IAM User account that can assume the AWS IAM Role for the integration.If your instance is deployed on AWS, the aws-sdk will automatically retrieve the credentials. Ensure that you assign the provided permission policy to your deployed instance, such as ECS or EC2.The following steps are for instances not deployed on AWS
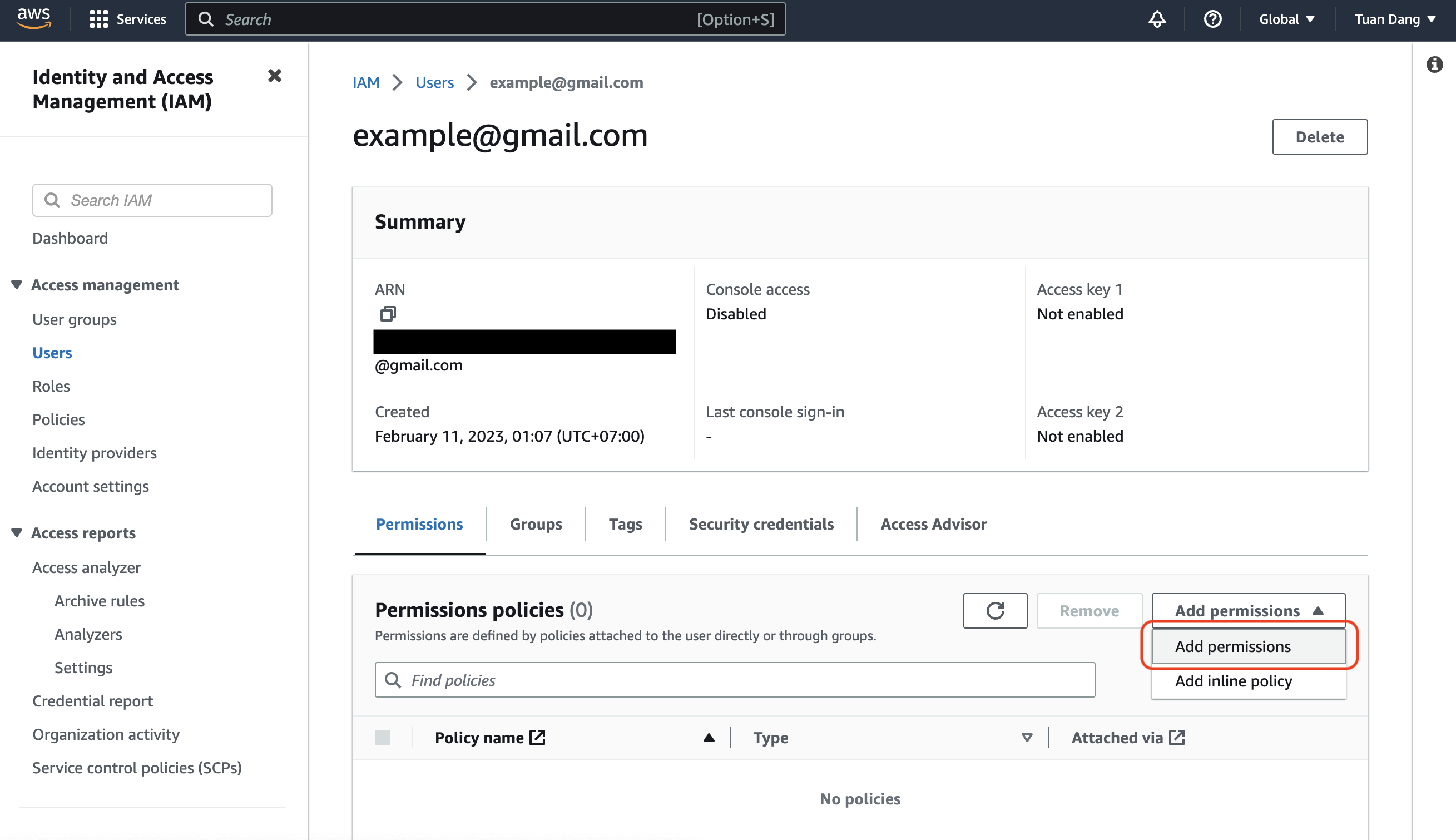
Create an IAM User
Navigate to Create IAM User in your AWS Console.
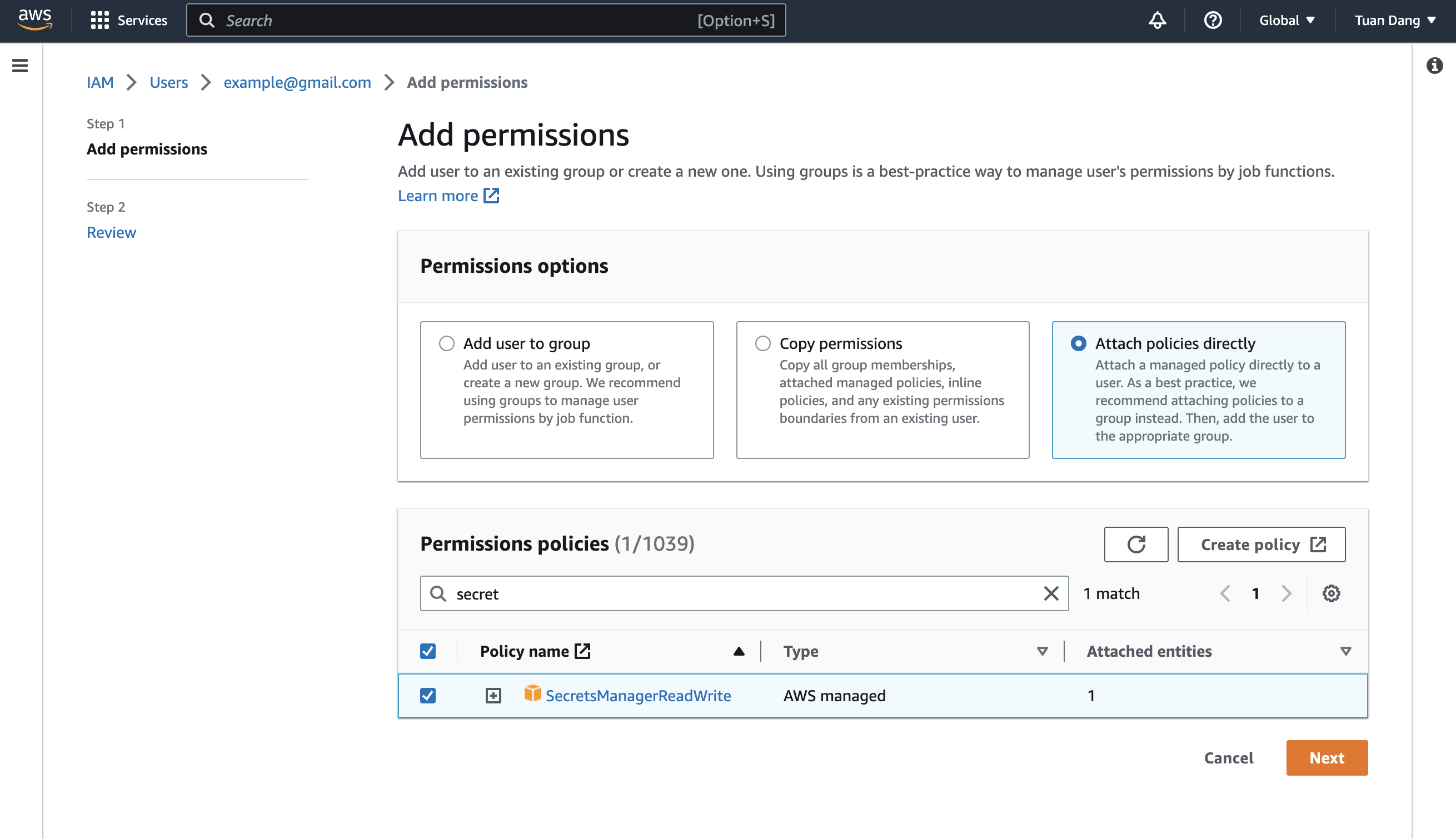
Create an Inline Policy
Attach the following inline permission policy to the IAM User to allow it to assume any IAM Roles:
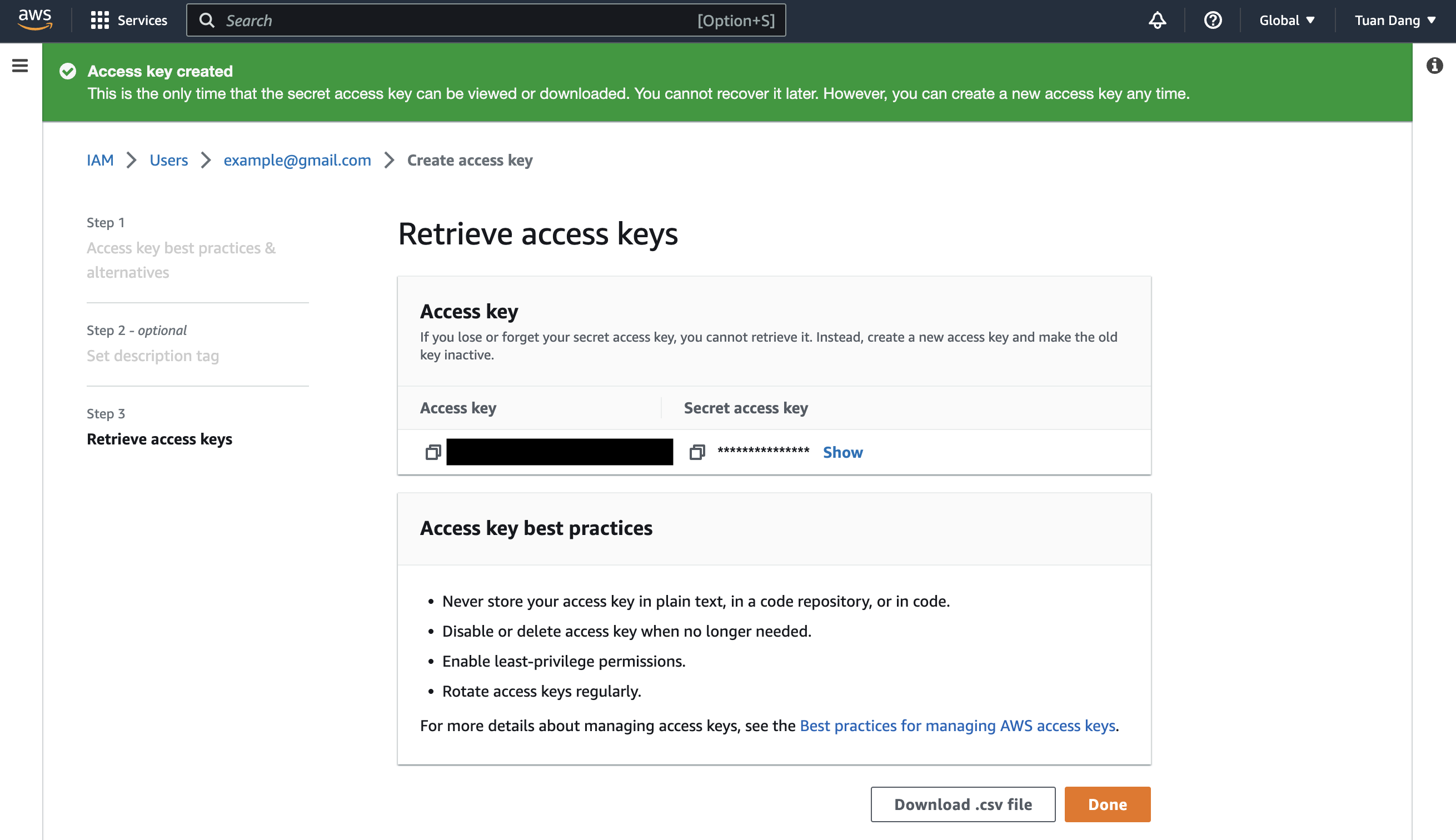
Obtain the IAM User Credentials
Obtain the AWS access key ID and secret access key for your IAM User by navigating to IAM > Users > [Your User] > Security credentials > Access keys.
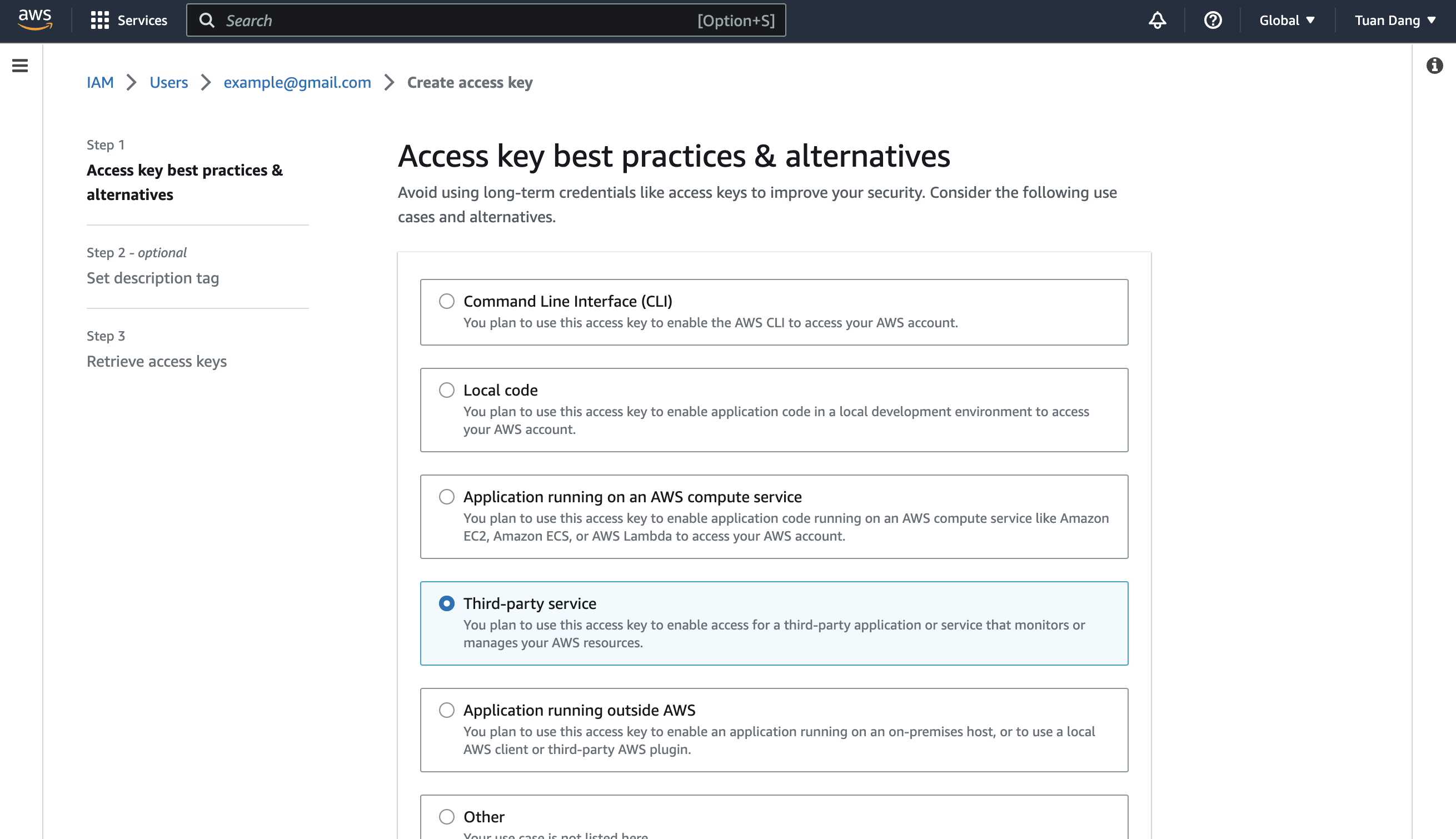



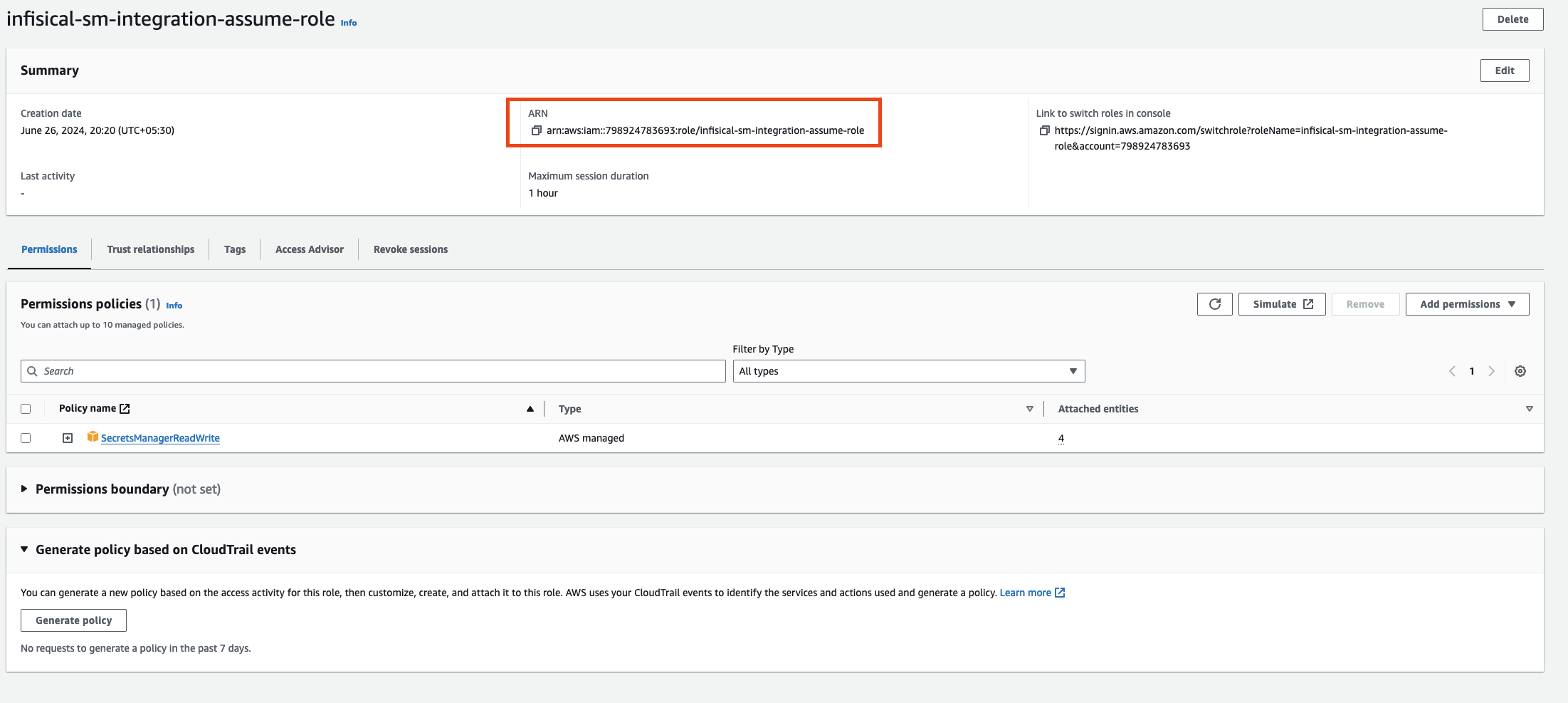
Create the Managing User IAM Role for AWS Secrets Manager
-
Navigate to the Create IAM Role page in your AWS Console.
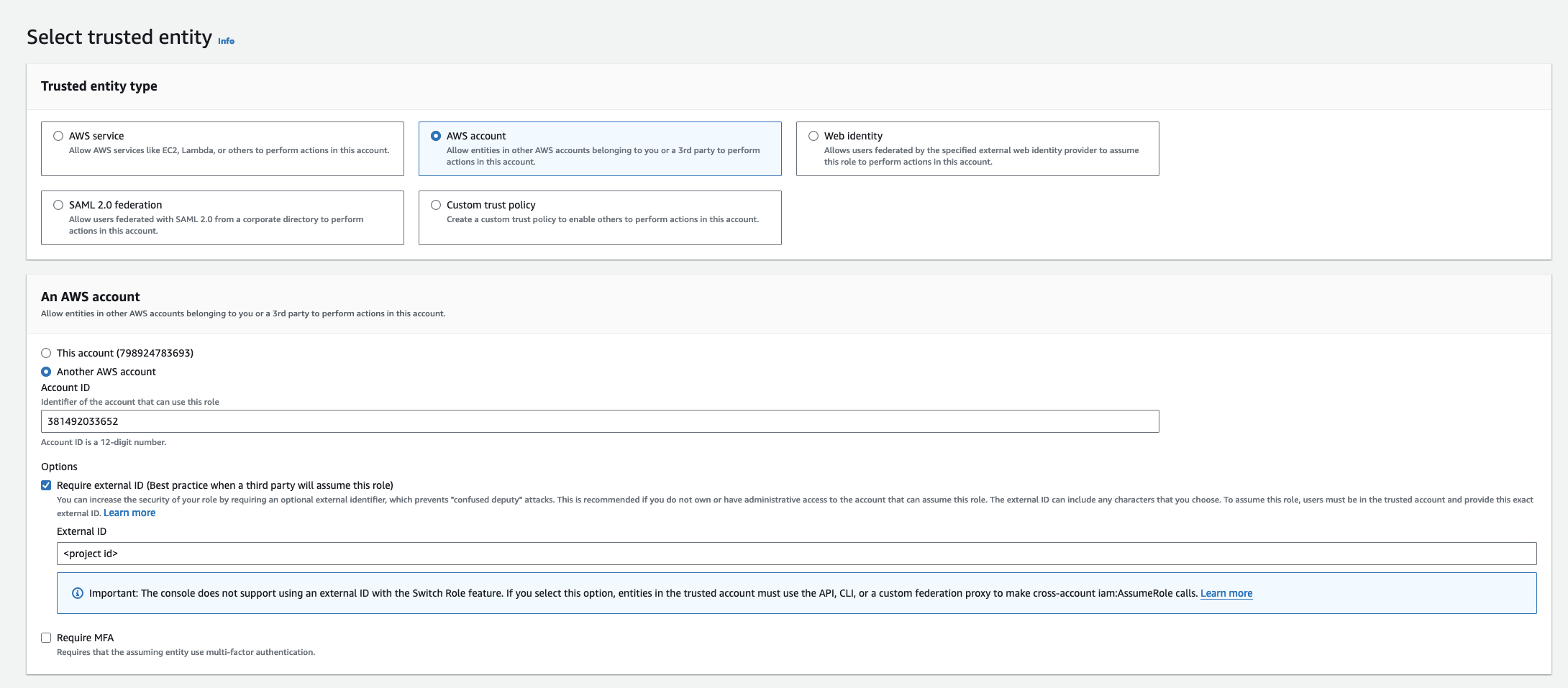
- Select AWS Account as the Trusted Entity Type.
- Choose Another AWS Account and enter 381492033652 (Infisical AWS Account ID). This restricts the role to be assumed only by Infisical. If self-hosting, provide your AWS account number instead.
- Optionally, enable Require external ID and enter your project ID to further enhance security.
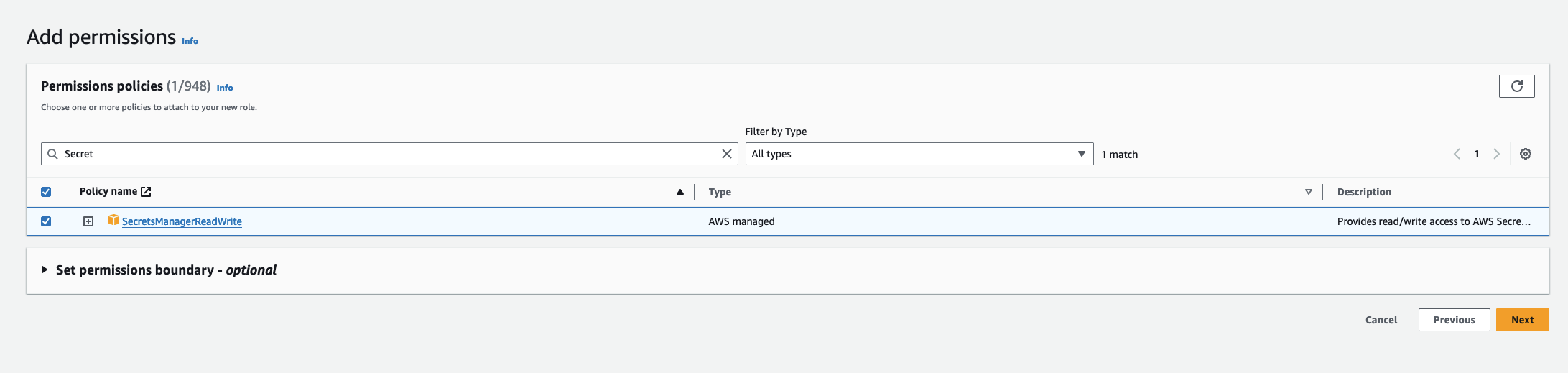
Add Required Permissions for the IAM Role
 Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Secrets Manager:
Use the following custom policy to grant the minimum permissions required by Infisical to sync secrets to AWS Secrets Manager:Authorize Infisical for AWS Secrets Manager
- Navigate to your project’s integrations tab in Infisical.
-
Click on the AWS Secrets Manager tile.

-
Select the AWS Assume Role option.
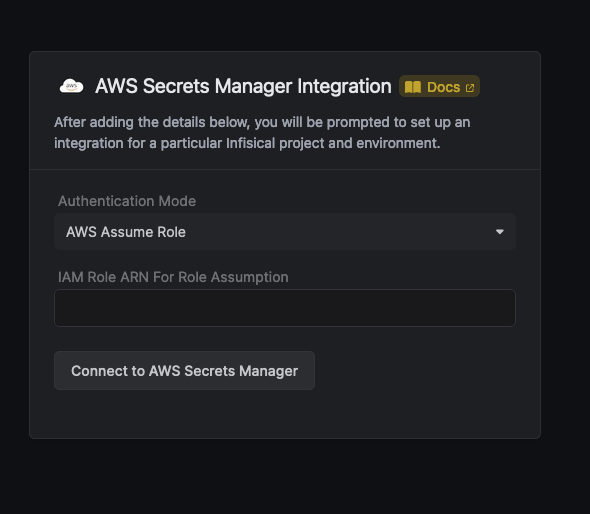
- Provide the AWS IAM Role ARN obtained from the previous step.
Start integration
Select how you want to integration to work by specifying a number of parameters: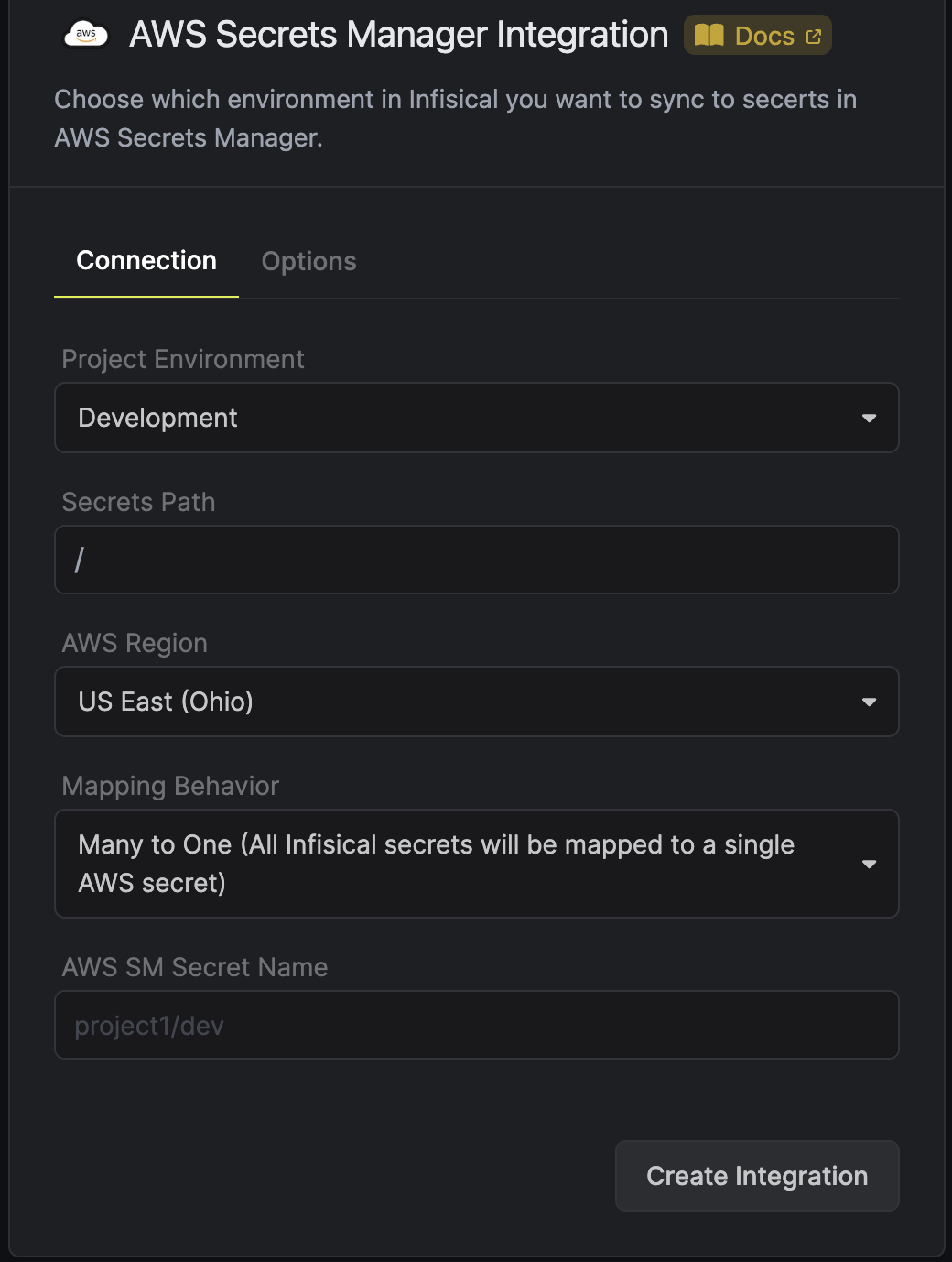 Optionally, you can add tags or specify the encryption key of all the secrets created via this integration:
Optionally, you can add tags or specify the encryption key of all the secrets created via this integration: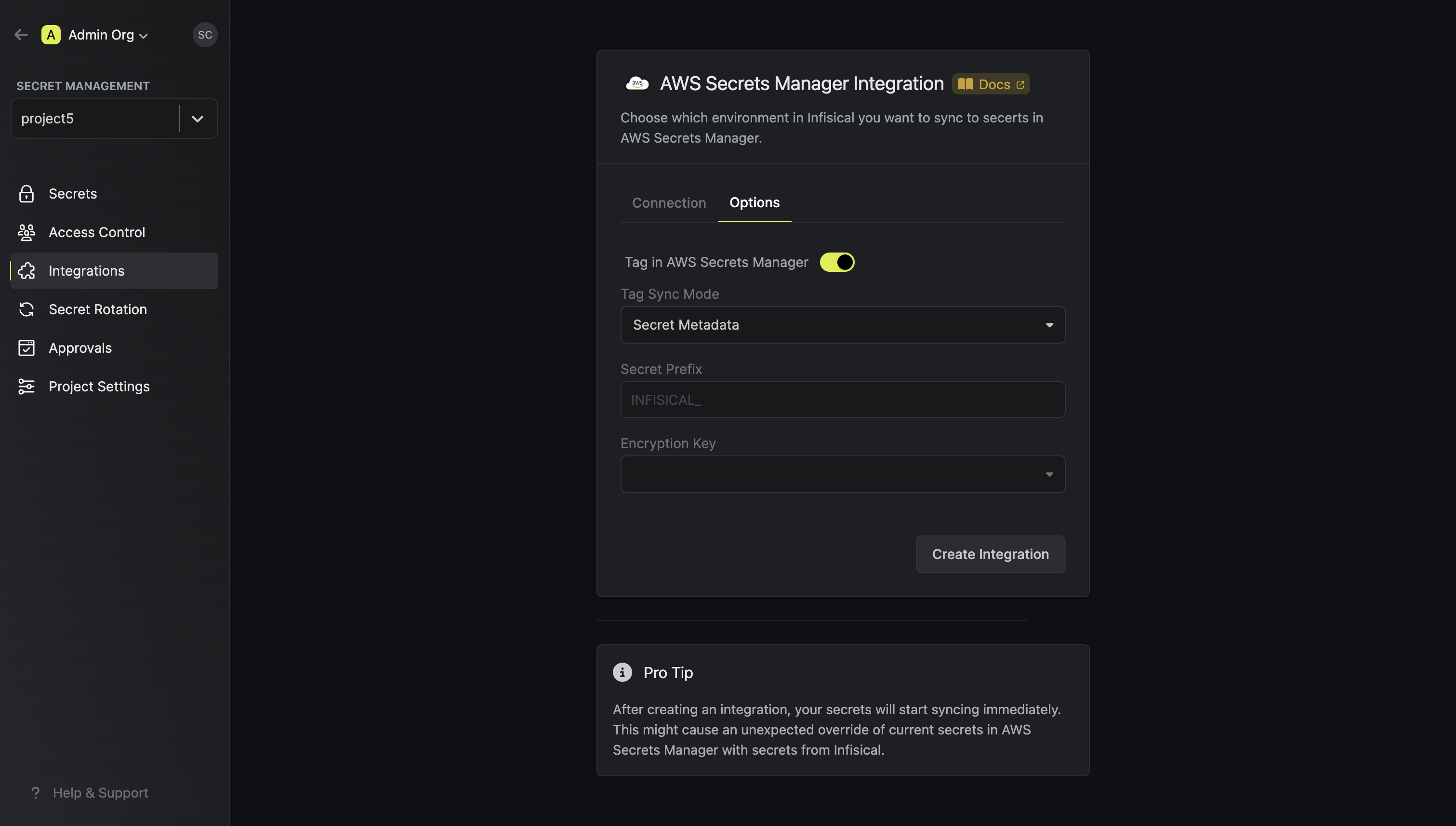 Then, press
Then, press
The environment in Infisical from which you want to sync secrets to AWS Secrets Manager.
The path within the preselected environment form which you want to sync secrets to AWS Secrets Manager.
The region that you want to integrate with in AWS Secrets Manager.
How you want the integration to map the secrets. The selected value could be either one to one or one to many.
The secret name/path in AWS into which you want to sync the secrets from Infisical.
 Optionally, you can add tags or specify the encryption key of all the secrets created via this integration:
Optionally, you can add tags or specify the encryption key of all the secrets created via this integration:The sync mode for AWS tags. The supported options are
Secret Metadata and Custom. If Secret Metadata is selected,
the metadata of the Infisical secrets are used as tags in AWS. If custom is selected, then the key/value of the Secret Tag field is used. Secret Metadata mode
is only supported for one-to-one integrations.The Key/Value of a tag that will be added to secrets in AWS. Please note that it is possible to add multiple tags via API.
The alias/ID of the AWS KMS key used for encryption. Please note that key should be enabled in order to work and the IAM user should have access to it.
 Then, press
Then, press Create Integration to start syncing secrets to AWS Secrets Manager.Infisical currently syncs environment variables to AWS Secrets Manager as
key-value pairs under one secret. We’re actively exploring ways to help users
group environment variable key-pairs under multiple secrets for greater
control.
Please note that upon deleting secrets in Infisical, AWS Secrets Manager immediately makes the secrets inaccessible but only schedules them for deletion after at least 7 days.